Loading...
Searching...
No Matches
pip._vendor.urllib3.connection Namespace Reference
Data Structures | |
| class | BaseSSLError |
| class | BrokenPipeError |
| class | ConnectionError |
| class | DummyConnection |
| class | HTTPConnection |
| class | HTTPSConnection |
Functions | |
| _match_hostname (cert, asserted_hostname) | |
| _get_default_user_agent () | |
Variables | |
| BaseSSLError = ssl.SSLError | |
| ssl = None | |
| ConnectionError = ConnectionError | |
| BrokenPipeError = BrokenPipeError | |
| log = logging.getLogger(__name__) | |
| dict | port_by_scheme = {"http": 80, "https": 443} |
| RECENT_DATE = datetime.date(2022, 1, 1) | |
| _CONTAINS_CONTROL_CHAR_RE = re.compile(r"[^-!#$%&'*+.^_`|~0-9a-zA-Z]") | |
| HTTPSConnection = DummyConnection | |
| VerifiedHTTPSConnection = HTTPSConnection | |
Function Documentation
◆ _get_default_user_agent()
|
protected |
Definition at line 558 of file connection.py.
558def _get_default_user_agent():
559 return "python-urllib3/%s" % __version__
560
561
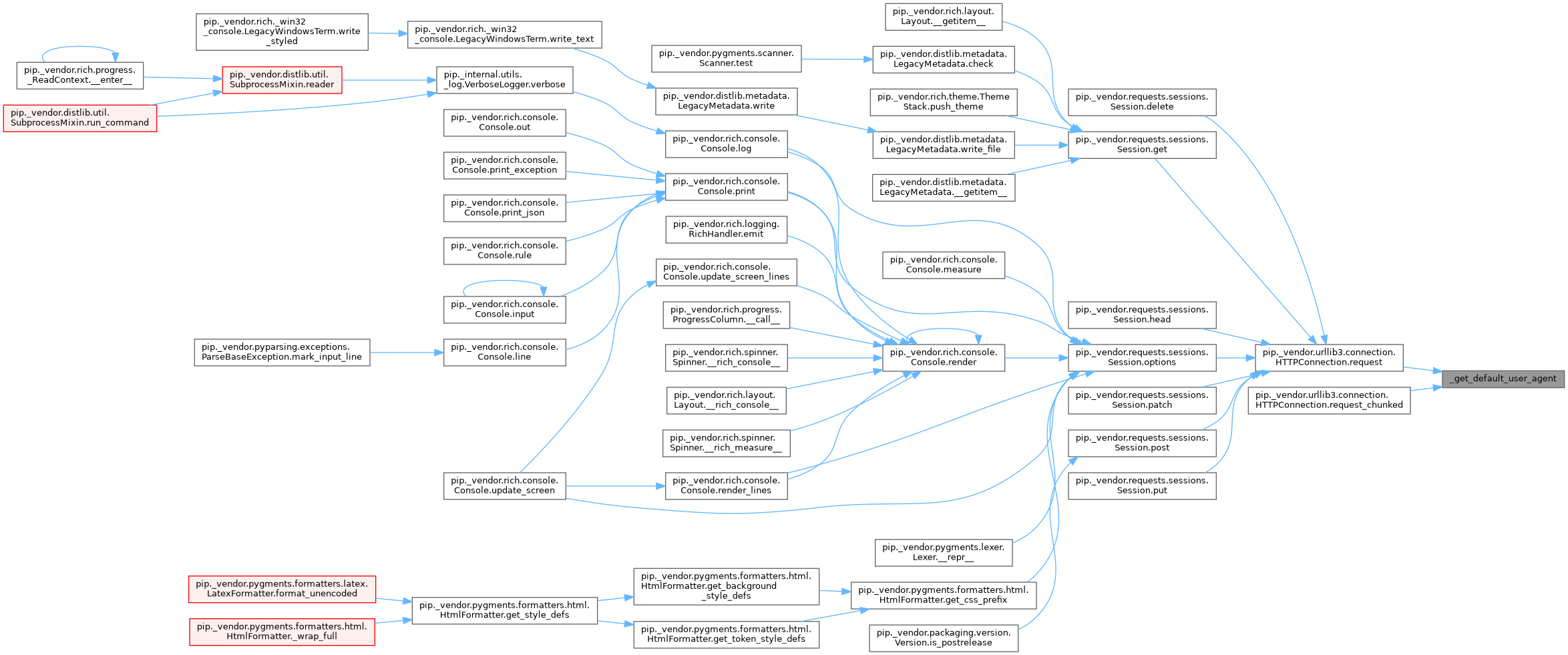
Referenced by HTTPConnection.request(), and HTTPConnection.request_chunked().
Here is the caller graph for this function:
◆ _match_hostname()
|
protected |
Definition at line 536 of file connection.py.
536def _match_hostname(cert, asserted_hostname):
537 # Our upstream implementation of ssl.match_hostname()
538 # only applies this normalization to IP addresses so it doesn't
539 # match DNS SANs so we do the same thing!
541 if is_ipaddress(stripped_hostname):
542 asserted_hostname = stripped_hostname
543
544 try:
545 match_hostname(cert, asserted_hostname)
546 except CertificateError as e:
547 log.warning(
548 "Certificate did not match expected hostname: %s. Certificate: %s",
549 asserted_hostname,
550 cert,
551 )
552 # Add cert to exception and reraise so client code can inspect
553 # the cert when catching the exception, if they want to
554 e._peer_cert = cert
555 raise
556
557
References i.
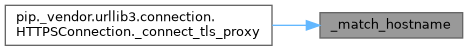
Referenced by HTTPSConnection._connect_tls_proxy().
Here is the caller graph for this function:
Variable Documentation
◆ _CONTAINS_CONTROL_CHAR_RE
Definition at line 73 of file connection.py.
◆ BaseSSLError
| BaseSSLError = ssl.SSLError |
Definition at line 20 of file connection.py.
◆ BrokenPipeError
Definition at line 39 of file connection.py.
◆ ConnectionError
Definition at line 30 of file connection.py.
◆ HTTPSConnection
Definition at line 569 of file connection.py.
◆ log
| log = logging.getLogger(__name__) |
Definition at line 65 of file connection.py.
◆ port_by_scheme
| dict port_by_scheme = {"http": 80, "https": 443} |
Definition at line 67 of file connection.py.
◆ RECENT_DATE
| RECENT_DATE = datetime.date(2022, 1, 1) |
Definition at line 71 of file connection.py.
◆ ssl
| ssl = None |
Definition at line 22 of file connection.py.
◆ VerifiedHTTPSConnection
| VerifiedHTTPSConnection = HTTPSConnection |
Definition at line 572 of file connection.py.